- Key Concepts
- Understanding edgeEngine Tokens
Understanding edgeEngine Tokens
Purpose
The purpose of this document is to describe the various tokens that are used when working in the edgeEngine computing environment.
Intended Readers
The intended readers of this document are software developers, system engineers, application architects, deployment personnel, and other technical professionals who want to understand the details of working with the various tokens that are part of the edgeEngine computing environment.
What You Will Learn from this Document
After reading this document, you will:
- Understand the purpose of tokens within the edgeEngine Runtime environment
- Have a working knowledge of a Developer ID Token as used when working with the edgeEngine Runtime
- Have a working knowledge of an Access Token as used when working with the edgeEngine Runtime
- Understand the relationship between a Developer ID Token and an Access Token
What You Need to Know Before You Start
In order to get the full benefit from reading this document, you need to have:
- A general understanding of token based security and token-based authentication
- An understanding of the edgeEngine Runtime and how it supports microservices
Working with the edgeEngine Tokens
The way the edgeEngine Runtime implements identity and security is by using tokens. There are two types of tokens used by the edgeEngine Runtime. These tokens are the ID Token and the Access Token. The following sections describe the details of each.
Developer ID Token
The Developer ID Token is a unique UUID the identifies the user account within the edgeEngine Runtime environment. The ID Token is created within the mimik Developer Console Dashboard, as shown below in Figure 1.
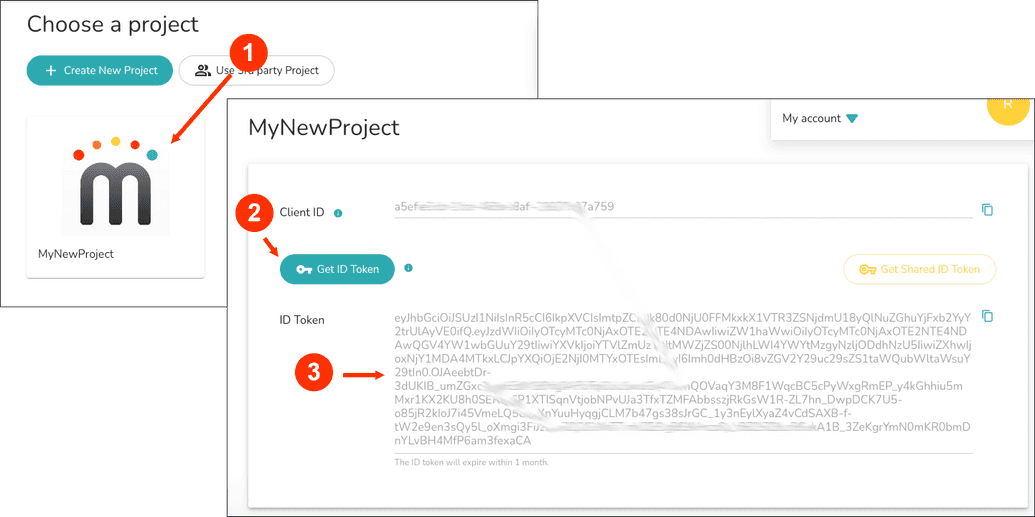
|
|---|
| Figure 1: The ID Token is a UUID that's created in the Mimik Developer Console |
Once the Developer ID Token is created, a developer uses it to create an Access Token. The Access Token is created from within a device running the edgeEngine Runtime at the command line. The Access Token is created using the mimik-edge-cli Tool.
Access Token
The Access Token is the artifact that binds the user account, as represented by the Developer ID Token, to the device on which the edgeEngine Runtime is functioning. As mentioned above, you'll use the mimik-edge-cli
ool to create the Access Token.
Working with the Access Token is a two-step process. First, you need to request an Access Token using the mimik-edge-cli Tool. Then, you'll need to associate the Access Token in order to implement secure ownership of a communication channel internally within and externally to the edge node.
The command to request an Access Token using the mimik-edge-cli Tool is as follows:
mimik-edge-cli account get-edge-access-token -t <ID_TOKEN>
For example:
mimik-edge-cli account get-edge-access-token -t eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjV2RG45aF9LSHNxTkJZNVZubUxFd0VfUVNpQTkzZEYyN1FTQUVRdVl5T2sifQ.eyJzdWIiOiIyODE0MzA0ODA1MTkyNjAxNjAwIiwiZW1haWwiOiIyODE0MzxxxA1MTkyNjAxNjAwQGV4YW1wbGUuY29tIiwiYXVkIjoiYmI2ZmJhN2QtNjMyMS00MWM1LWFjMzctMWE3YThhOWE0YWMwIiwiZXhwIjoxNjIzNDYxOTA2LCJpYXQiOjE2MjA4Njk5MDYsImlzcyI6Imh0dHBzOi8vbWlkLm1pbWlrMzYwLmNvbSJ9.dM2mIK6aw9jSA02Pk-MzhjBrPsSPOWX-PGAP3x5lArVwz_VSz1nal7UFh08onpiK1_Gvnd_npounbNQJcQTs5f6F0oqtHvifubC84QnOKHf6D1-zLnC4VUiEp8v24Ys5AF0DYfU7DkA7n77l5YL-IeV2O7VWJpw1ELyCa-WW7ya2L1kukcX0zJ8naKljxeXA9LERHPTuzyx6mbGyz4YgsGGJxMJ3X3XdujhzETR-FXcxemc4zh4y1FhcbjOJDoJN7peB1fWQGlr3AXIFXiiLJ4EWyHPoQ7q8sf8kqAaJB05lsh5OpuWRjWLjqdHvmKEm-aw1poArVW_4dTtaIx8eqw --use-mid-v1
Upon successful execution, you'll get a response with the Access Token similar to the following:
access_token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIyODE0MzA0ODA1MTkyNjAxNjAwIiwianRpIjoiQX5uY3ZUZVhITU9ieGx-NEE1bmZ2eUVIdEpZNGJzcUNMWGl5RVpSYk1PUSIsImNsaWVudF9pZCI6ImJiNmZiYTdkLTYzMjEtNDFjNS1hYzM3LTFhN2E4YTlhNGFjMCIsImF6cCI6ImJiNmZiYTdkLTYzMjEtNDFjNS1hYzM3LTFhN2E4YTlhNGFjMCIsImlzcyI6Imh0dHBzOi8vbWlkLm1pbWlrMzYwLmNvbS9tSUQvdjEvb2F1dGgvdG9rZW4iLCJub2RlX2lkIjoiZTAwYWRhYzU4ODMzODFhZDVjMmYxMDE5MjEyYzRmOTU0ZjI3NWY1ZjNkOWIzMDZlNTcxMjhlYWQiLCJhdWQiOlsiaHR0cHM6Ly9taW1payIsImh0dHBzOi8vbXN0Lm1pbWlrMzYwLmNvbS9tU1QvdjEvY2xpZW50cy9HZW5lcmljLWVkZ2UiXSwic2NvcGUiOiJvcGVuaWQgZWRnZTptY20gZWRnZTpjbHVzdGVycyBlZGdlOmFjY291bnQ6YXNzb2NpYXRlIGVkZ2U6YWNjb3VudDp1bmFzc29jaWF0ZSBlZGdlOnJlYWQ6YWNjb3VudGtleSIsImlhdCI6MTYyMDg3MTczMCwiZXhwIjoxNjM2NDIzNzMwfQ.m28Z3fuIHR5UBC_vgFFpjGIHpl0t4J2RYsP0JUeq2p4
Once you have an Access Token in hand, you'll associate it with the node, using the following command:
mimik-edge-cli account associate -t <ACCESS_TOKEN>
For example:
mimik-edge-cli account associate -t eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIyODE0MzA0ODA1MTkyNjAxNjAwIiwianRpIjoiQX5uY3ZUZVhITU9ieGx-NEE1bmZ2eUVIdEpZNGJzcUNMWGl5RVpSYk1PUSIsImNsaWVudF9pZCI6ImJiNmZiYTdkLTYzMjEtNDFjNS1hYzM3LTFhN2E4YTlhNGFjMCIsImF6cxxxxxmZiYTdkLTYzMjEtNDFjNS1hYzM3LTFhN2E4YTlhNGFjMCIsImlzcyI6Imh0dHBzOi8vbWlkLm1pbWlrMzYwLmNvbS9tSUQvdjEvb2F1dGgvdG9rZW4iLCJub2RlX2lkIjoiZTAwYWRhYzU4ODMzODFhZDVjMmYxMDE5MjEyYzRmOTU0ZjI3NxxxxxkOWIzMDZlNTcxMjhlYWQiLCJhdWQiOlsiaHR0cHM6Ly9taW1payIsImh0dHBzOi8vbXN0Lm1pbWlrMzYwLmNvbS9tU1QvdjEvY2xpZW50cy9HZW5lcmljLWVkZ2UiXSwic2NvcGUiOiJvcGVuaWQgZWRnZTptY20gZWRnZTpjbHVzdGVycyBlZGdlOmFjY291bnQ6YXNzb2NpYXRlIGVkZ2U6YWNjb3VudDp1bmFzc29jaWF0ZSBlZGdlOnJlYWQ6YWNjb3VudGtleSIsImlhdCI6MTYyMDg3MTczMCwiZXhwIjoxNjM2NDIzNzMwfQ.m28Z3fuIHR5UBC_vgFFpjGIHpl0t4J2RYsP0JUeq2p4
Successful association of the Access Token will yield the response:
1: {2: "result": {3: "accountId": "2814304805192601600"4: },5: "status": "successfully associated"6: }
You are now ready to use the Access Token to authenticate the microservices you'll be creating to run under the edgeEngine Runtime. You can view tutorials demonstrating various aspects of programming edgeEngine microservices in the Tutorials section of this Developer Portal Documentation.
The important thing to remember about edgeEngine Tokens is that the Developer ID Token identifies the user account as generated within the mimik Developer Console. And, you'll use the Developer ID Token to request an Access Token using the mimik-edge-cli Tool from within a device running the edgeEngine Runtime.
You'll associate the Access Token to the device running the edgeEngine Runtime using the mimik-edge-cli Tool. The purpose of the Access Token is to secure ownership of a communication channel to the device that's running the edgeEngine Runtime.